Guide on HIPAA Compliance for Software: Key Security Controls and Their Implementation
Editor’s note: In this article, Alena explains what it means to make healthcare software HIPAA-compliant and illustrates a real-world implementation of HIPAA security controls in collaboration platforms, like Zoom, as well as in ScienceSoft’s own projects. If you are looking to develop a HIPAA-compliant and secure healthcare software, ScienceSoft delivers a full range of healthcare software development services.

Only 6% of Covered Entities Had Compliant Software in the Last HIPAA Audit Round
After a long hiatus due to limited resources, the HHS Office for Civil Rights (OCR) launched the third phase of HIPAA audits in late 2024, and it’s expected to continue through the end of 2025. The results of the second phase, conducted from 2016 to 2017, were disappointing — most entities failed to achieve HIPAA compliance. Notably, the software systems of only 6% of organizations and 12% of business associates had all the required technical safeguards in place to protect electronic patient health information (ePHI).
Has the situation changed in 2025? A recent survey found that only 39% of healthcare providers felt “very prepared” for HIPAA audits.
Meanwhile, US healthcare data breach statistics continue to break records. In 2024, 734 major data breaches (involving 500 or more patient records) were reported. Over 275 million patient records were compromised, meaning a staggering 82% of the US population was affected. 81% of all 2024 data breaches were caused by hacking.
In 2024, 22 healthcare providers and business associates were penalized by the OCR for HIPAA violations, with fines ranging from $10,000 to $4.5 million. But regulatory fines are only part of the impact. Victims of cyberattacks also face losses from downtime, ransom payments, and the costs of recovery efforts. According to IBM's report, the average cost of a healthcare data breach in the US is $10.93 million.
What Makes Software HIPAA-Compliant?
HIPAA compliance for software means meeting HIPAA security standards to protect sensitive health information that is stored or transmitted in electronic form by healthcare software systems. These standards are defined in the HIPAA Security Rule, specifically in the section known as Technical Safeguards. In practice, this means healthcare software should have security capabilities, such as access control, activity auditing, and data encryption, which protect data from being accessed by unauthorized and potentially malicious users, track suspicious activity (e.g., repeated failed login attempts) to prevent breaches, and ensure data confidentiality when it’s stored or transferred.
However, implementing technical safeguards in software is only one step towards achieving HIPAA compliance. Under the HIPAA Security Rule, a covered entity should also enforce Administrative and Physical Safeguards. These include such critical measures as protecting physical devices that store data, ensuring medical staff follow established security policies and procedures, regularly assessing vulnerabilities in the organization’s and its vendors’ software, and evaluating risks when adopting new digital services.
To provide a comprehensive understanding of HIPAA compliance requirements, I’ve prepared an overview of the three types of safeguards: technical, administrative, and physical. I’ll begin with a closer examination of the technical measures applicable to healthcare software.
Measures to Ensure HIPAA Compliance of Healthcare Software
Below, I outlined technical safeguards that must be implemented in healthcare software to achieve HIPAA compliance and protect PHI.
- Data access control involves setting up user roles, multi-factor user authentication, access rights, action permissions, automatic logoff, and other measures. Such measures help restrict system access according to role-specific and user-specific permissions, so you can achieve patient data privacy and minimize the possibility of its leakage.
- Data encryption means translating the patient data in transit and at rest into a form that cannot be decrypted by unauthorized users or by anyone who does not have the encryption key. There are various types of data encryption, including file-level, block-level, and database-level encryption. They are divided based on which part of the data or system is being encrypted (e.g., individual files, entire storage blocks, or specific database fields), and are applied depending on the specific security needs and system performance requirements.
- Detailed access logging requires recording all transactions involving PHI, including user logins and logouts, record access, creation, deletion, edits, and transfers. These logs help detect suspicious user or system activity (e.g., large downloads or repeated failed login attempts) and identify breaches early.
- Integrity control refers to the process of checking the integrity of ePHI (e.g., using checksums or digital signatures) when received, before storage, and after transfers, along with logging of integrity checks. This is essential to confirm ePHI isn’t altered or destroyed by accident or with malicious intent.
- Secure transmission means using safeguards, such as encryption, when transmitting PHI between systems over open networks. If the application sends emails or SMS to users, secure email portals and encrypted messaging must be used.
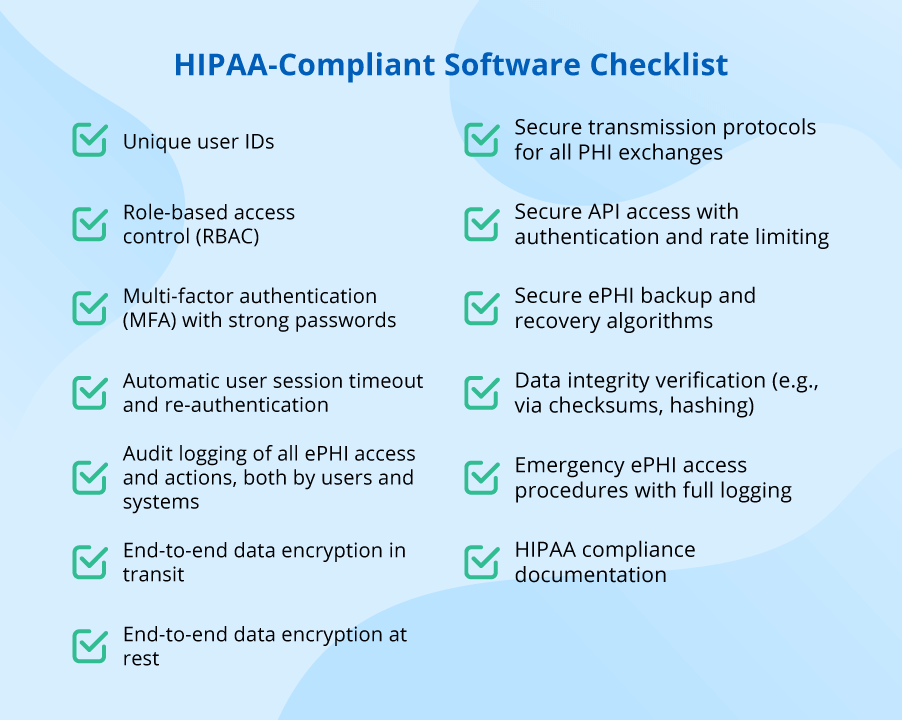
In addition to the overview of the required technical safeguards, our team has prepared a HIPAA-compliant software checklist that outlines the key security features typically implemented in healthcare software. You can use it to quickly assess if your systems have all the needed security controls in place:
Administrative and Physical Security Controls for Achieving HIPAA Compliance
Physical and administrative safeguards matter just as much as technical ones, since patient data leaks can also happen for many other reasons, not just because the healthcare software isn't secure enough. For example, here are some common weak points that can be prevented with proper administrative and physical safeguards:
- Organization’s devices, when not physically secured, can be stolen or improperly disposed of, which then results in a data breach. According to the OCR report, healthcare providers have made real progress here — the number of such breaches fell from 163 in 2014 to 22 in 2024.
- Cloud infrastructure has now turned into a vulnerability point for healthcare providers. According the 2024 Ponemon Institute study, 63% of the 648 US organizations surveyed said they feel vulnerable or highly vulnerable to their cloud software being compromised, and 69% reported having experienced such incidents, with an average of 20 cases over the past two years.
- Workforce security continues to be a key weak spot for healthcare organizations, since the most common entry point for cyberattacks is phishing. Phishing schemes were part of over 90% of cyberattacks, and in 2024, more than 80% of healthcare organizations had at least one successful phishing incident.
- Third-party compromises are the second most common cause of patient data breaches after ransomware, according to the Forescout report. Security flaws in systems of vendors, partners, and suppliers that are connected to a healthcare provider’s software are just as dangerous to the provider as its own vulnerabilities.
To address these security risks, healthcare organizations must have policies and procedures in place that include all the administrative and physical safeguards required by HIPAA. Below, we provide a brief description of such safeguards; for further specifics, you can consult the industry guidelines.
Administrative safeguards
- Designated security officer: appointing a person in charge of creating and revising the organization's security policies and procedures, as well as their enforcement through internal audits.
- Information access control: authorizing access to ePHI only for the minimum necessary number of employees, and only when they need it to perform their duties.
- Security monitoring and testing: constant system log monitoring to identify security incidents, regular software and infrastructure vulnerability assessments, and regular penetration testing, with timely patching of the detected software vulnerabilities.
- Security incident procedures: creating an action plan to mitigate harm in the event of a suspected or known incident, e.g., by blocking unauthorized access to patient records, notifying administrators about suspicious login attempts, or isolating infected devices on the hospital network.
- Contingency planning: implementing procedures to back up data and recover any lost ePHI; an emergency plan in case of interruptions to critical business operations.
- Workforce security: policies and procedures for identifying the lowest necessary access level to ePHI, supervising employees who have access to ePHI, and revoking access rights after employment termination.
- Security awareness and training: training all employees on handling ePHI, using passwords securely, identifying phishing attempts, and browsing safely; discussing security incidents with staff to explain how to avoid them; enforcing disciplinary measures against those who violate the organization's security rules.
- Business associate contracts: signing a written agreement about implementing HIPAA-compliant safeguards with any vendor or partner before permitting them to access or handle patients' ePHI.
- Security risk management: ongoing analysis of potential vulnerabilities in new and existing software; updating security policies when necessary; monitoring employee compliance with security procedures and resolving any existing gaps in the policies.
Physical Safeguards
- Secure hosting environment: hosting healthcare software on a secure, HIPAA-compliant cloud that ensures proper physical protection of data servers and redundancy measures for data recovery in case of an emergency.
- Workstation security: physical safeguards (e.g., cable locks, screen filters, video monitoring) for all devices used by the organization’s personnel to access ePHI. These safeguards are aimed at preventing theft and unauthorized access.
- Device and media control: procedures for securely receiving hardware and electronic media (such as hard drives and USB drives) containing ePHI at a facility and properly removing them from the facility to prevent any ePHI compromise.
Popular Collaboration Platforms as Examples of HIPAA-Compliant Software
When implementing HIPAA safeguards, organizations often need to evaluate how to apply them on a case-by-case basis. One common challenge is determining how HIPAA applies when a healthcare organization introduces a third-party solution, such as a new collaboration tool, into its IT ecosystem. So, are Google Workspace, Microsoft Teams, and Zoom HIPAA-compliant? By default, no. Yet, at the same time, their providers offer healthcare organizations the option to use these convenient collaboration tools for tasks involving the sharing of ePHI, in full compliance with HIPAA.
However, several conditions must be met:
- Signing a Business Associate Agreement (BAA) with the platform provider that specifies which services, add-ons, and third-party integrations fall under HIPAA-compliant coverage.
- Applying specific security settings to the software that ensure strong, HIPAA-compliant ePHI protection.
- Training staff on using the software in a safe and compliant manner.
Google Workspace (Gmail, Drive, Calendar, Meet, etc.)
To meet HIPAA requirements when using Google Workspace, an organization must be on a paid plan (e.g., Business, Enterprise) and sign Google’s Business Associate Agreement (BAA), which is available in the admin console. After that, they need to follow Google’s HIPAA Implementation Guide to enable proper security controls. For example, in Gmail, this could include scanning emails for specific PHI markers and restricting their sharing to only approved addresses.
Microsoft Teams (part of Microsoft 365)
Microsoft has published a whitepaper on Teams for healthcare that outlines how to set security controls in Office 365 for HIPAA compliance. In brief, the organization must select a Microsoft 365 plan that supports HIPAA compliance (e.g., Business Premium, E3, E5), sign a BAA with Microsoft, and configure the services in line with HIPAA requirements. For example, Microsoft Teams supports HIPAA-compliant end-to-end encryption for individual video calls; however, to configure it, users must apply a specific setup and disable certain advanced features.
Zoom (Meetings and Chat)
Zoom offers a dedicated HIPAA-compliant plan (Zoom for Healthcare). After signing a BAA, Zoom can be used for telehealth, meetings, or chats involving PHI sharing. Zoom provides encryption and all other necessary HIPAA controls. No additional manual configuration is required from healthcare organizations; all they need to do is educate staff to refrain from recording or sharing ePHI without safeguards.
HIPAA-Compliant Software Development Projects by ScienceSoft
Now, let’s see how ScienceSoft’s team implements the principles of HIPAA compliance in real-life software development projects.
ScienceSoft designed an Android telehealth application for Chiron Health, a widely known telemedicine solution provider. The app enables patients to book appointments and get video and audio medical consultations from their physicians. To ensure HIPAA compliance of the telehealth app, we applied:
- Password protection.
- Establishing user roles (a patient, a physician, an admin) with particular permission settings.
- Logging via email/phone verification code.
- In-transit encryption of peer-to-peer video connection using the HTTPS protocol for communication with the server.
ScienceSoft developed an iOS mobile application for a European provider of mobile patient engagement software. The mobile app provides inpatients with secure access to their health history, lab results, and medications, enables communication with caregivers, and offers entertainment activities. Here are some of the measures we applied to make the app HIPAA-compliant:
- PIN code protection (set up by a patient’s case manager).
- Establishing user roles (a patient, a physician, a nurse, a case manager) with particular permission settings.
- Establishing secure communication channels (text, image, and voice messages, video conferencing) with the help of data encryption in transit.
HIPAA Compliance Software (Not to Be Confused With HIPAA-Compliant Software)
Finally, I would like to discuss HIPAA compliance software. People often confuse it with HIPAA-compliant software because the terms sound similar, even though they mean two completely different things.
HIPAA-compliant software, as previously discussed, refers to any system that securely protects sensitive patient data (ePHI) in accordance with HIPAA requirements.
HIPAA compliance software (or HIPAA compliance assessment tools), on the other hand, refers to useful tools that help healthcare organizations and their vendors evaluate their policies, procedures, and technical controls against HIPAA requirements. Such tools can be used to conduct internal audits, assess data breach risks, and identify gaps in their security systems.
Here are some examples of popular HIPAA compliance solutions.
HHS Security Risk Assessment (SRA) Tool is a free desktop app that guides an organization through the HIPAA risk assessment process using a step-by-step wizard. The wizard asks structured questions about healthcare providers’ security policies and the technical controls of their software, helping them to assess security risks. It’s an official government tool, so it aligns with HHS expectations. However, it doesn't offer any automation; it’s just a question-based guide.
The Guard by Compliancy Group is a cloud-based HIPAA compliance platform that offers a range of tools that aid healthcare organizations in achieving and maintaining HIPAA compliance. Apart from guided risk assessment wizards, it provides customizable policy templates, ready-made staff training materials, and tools for managing the training process. It also offers dashboards for managing incidents, tracking remediation tasks, and monitoring agreements with vendors (incl. BAA). Upon completing their compliance program, Compliancy Group grants clients its own badge of compliance.
ControlMap, Drata, and Vanta are modern compliance automation platforms covering not only HIPAA, but also other security standards and regulations (e.g., SOC 2, ISO 27001, GDPR, PCI DSS). These platforms integrate with core IT ecosystem components (cloud infrastructure, identity and access management tools, endpoint management systems) to automatically map all of the technical controls in a centralized database. Apart from gathering this data, these platforms enable users to continuously monitor the controls’ configurations, conduct internal and third-party audits, and generate compliance reports populated with consolidated evidence. For example, Vanta automatically collects evidence of data encryption and MFA implementation, which helps prepare for a HIPAA audit.
HIPAA-Compliant Software FAQ
What makes a system HIPAA-compliant?
A system is considered HIPAA-compliant if it includes all the required HIPAA safeguards for protecting PHI. For software, this usually means encrypted PHI storage and transmission, strong access controls (such as unique logins and MFA), detailed user activity logs, regular backups, and disaster recovery mechanisms. It also requires organizational and personnel-level safeguards such as HIPAA training, signing BAAs with all the vendors of an organization, an incident response plan, oversight to ensure staff follow security policies, etc. In practice, compliance is demonstrated through documented risk assessments, internal policies, and regular audits.
Does HIPAA-compliant software ensure an organization's HIPAA compliance?
No, that’s a common misunderstanding. Having a HIPAA-compliant patient mobile app or telehealth platform means you’ve implemented only a part of the required security controls. To fully comply with HIPAA, your entire organization needs a setup with all types of safeguards — physical, administrative, and technical.
How do I make my computer HIPAA-compliant?
There's no such thing as a "HIPAA-compliant computer". What HIPAA actually requires is having specific technical safeguards in place and following certain usage rules to protect patient data from being disclosed. Technical safeguards typically include full disk encryption, up-to-date antivirus tools, software security patches, a firewall, encrypted channels for email and file-sharing clients, etc. Their implementation is the responsibility of a healthcare organization’s IT department. Medical staff using the computer are responsible for following the organization’s security procedures, such as installing only approved software, using strong passwords, and securing the computer (e.g., locking screens) when away.
Is HIPAA certification mandatory to ensure or prove HIPAA compliance?
No, that’s not true. Lots of HIPAA certification options on the market often mislead healthcare businesses. In fact, HIPAA compliance certificates aren’t officially recognized by the US government, and there’s no requirement to have them. Under the HIPAA Security Rule, HIPAA certification is just an optional method of testing or training for HIPAA compliance.
Avoid HIPAA Violations With Compliant Software!
HIPAA violations can lead to multimillion-dollar fines, damage your reputation, and undermine the trust of your patients or customers. I believe the safest way to prevent this is to work with a professional consulting and custom software development company that has a solid track record of delivering HIPAA-compliant healthcare solutions. Since 2005, ScienceSoft has been helping healthcare providers, diagnostic centers, and pharmaceutical and biotech research companies engineer solutions that achieve regulatory compliance. Contact us if you'd like to learn how we can assist in your specific case.

