How ScienceSoft Builds Interoperability Into Healthcare Software Ecosystems
We make your systems talk — and keep them talking. By designing interoperability into the architecture (FHIR/USCDI, SMART on FHIR, HL7, DICOM) and enforcing audited, encrypted data flows, you get real-time, vendor-neutral data exchange that stands up to HIPAA, Cures Act, and TEFCA.
Interoperability Risks Driven by Vendor Practices and How We Avoid Them by Design
What blocks interoperability isn't always technology; often it's flawed software vendor decisions. Below, we outline the most damaging vendor practices that not only disrupt healthcare data exchange but also compromise care delivery, inflate budgets, and expose organizations to avoidable legal risks.
We'll also highlight an interoperability-by-design, compliance-anchored approach that ensures integrations don't become a healthcare provider's weak spot.
|
|
What goes wrong |
How we make a difference |
|---|---|---|
|
Deliberate restriction of data exchange to enforce vendor lock-in
|
Many off-the-shelf EHRs and healthcare software platforms impose barriers to data exchange. For example, they may expose read-only or throttled APIs, omit key data fields, or limit access throughput, despite regulatory clarity against such tactics. These constraints drive up the cost and complexity of integrations, trap organizations in vendor ecosystems, and leave data fragmented across silos. |
Our custom software architectures are free of hidden integration barriers.
|
|
Integrations treated as an afterthought
|
In many healthcare software projects, integrations are treated as a secondary concern. They are implemented reactively (in response to requests) or late in development, sometimes post-MVP. The result is ad hoc integrations often relying on data polling, flat file exports, or generic middleware. They are fragile and often fail under real-world workloads, scale, or stricter compliance demands. |
We define integration logic during early-stage solution design, before features are built.
|
|
Compliance gaps in integration design
|
Custom software vendors often design integration logic blind to compliance requirements. Missing access controls, poor encryption practices, unlogged system interactions, or shared service accounts can expose PHI and violate HIPAA and other regulations. In cross-system integrations, when security responsibilities are blurred, audit trails are often incomplete or missing. As a result, covered entities face data breach risks and are forced to add necessary controls after deployment, under regulatory pressure. |
We treat integration points as compliance-controlled zones, not just technical utilities. From the API level up, we enforce HIPAA, HITECH, and other relevant regulations.
|
|
Insufficient validation of data exchange
|
In healthcare projects, integration testing is often deprioritized or excluded from the scope entirely. E.g., vendors only validate the fact of connection (message received) without verifying data completeness, field mapping, or impact on workflows. As a result, data gaps, semantic mismatches, or process disruptions surface only after go-live, requiring costly fixes under real-world pressure. |
We verify every layer of integration during system testing.
|
ScienceSoft's System-Level Approach to Healthcare Interoperability
How we architect interoperability into every system
In every healthcare software project we deliver, interoperability is embedded into the system architecture. Below, we describe how we build scalable, standards-based integration capabilities that remain robust across evolving regulations and workflows.
How we recover interoperability in fragmented environments
Many healthcare IT ecosystems are burdened by brittle HL7 feeds, proprietary interfaces, and inconsistent terminology layers. We help re-establish interoperability across these fragmented landscapes using modular, non-disruptive approaches that preserve clinical workflows while enabling modern data use.
FHIR adapters for legacy systems
We build middleware layers that act as FHIR-compatible gateways for legacy systems. These adapters translate modern FHIR-based requests into existing formats like HL7 v2/v3, SQL, or proprietary APIs while leaving legacy code untouched to reduce regression risks. Over time, direct HL7 interfaces can be deprecated to centralize integration logic and decouple business processes from outdated systems.
Centralized integration and terminology hubs
For projects involving multiple systems, we implement integration engines to streamline message routing and transformation. When needed, we include a terminology server to map custom or local codes to healthcare standards like SNOMED CT, LOINC, RxNorm, and ICD-10. This architecture reduces long-term maintenance costs and ensures consistent data exchange.
Data consolidation for healthcare analytics
We can build a healthcare data warehouse consolidating clinical and operational data from systems like EHR, LIS, RIS, and claims modules using ETL/ELT pipelines. It provides secure, HIPAA-compliant storage with role-based access and supports standard data formats such as FHIR and OMOP. The platform enables real-time analytics, BI integration, and predictive modeling, and can be deployed in the cloud, on-premises, or hybrid infrastructures.
Safe dual-run interface migration
When replacing outdated interfaces, we follow a dual-run approach where newly developed integrations operate in parallel with legacy ones. Traffic is switched gradually in small segments, with rollback options at each stage to prevent service disruption. All transformations are validated using synthetic data and real-world edge cases to ensure accuracy and continuity throughout the migration process.
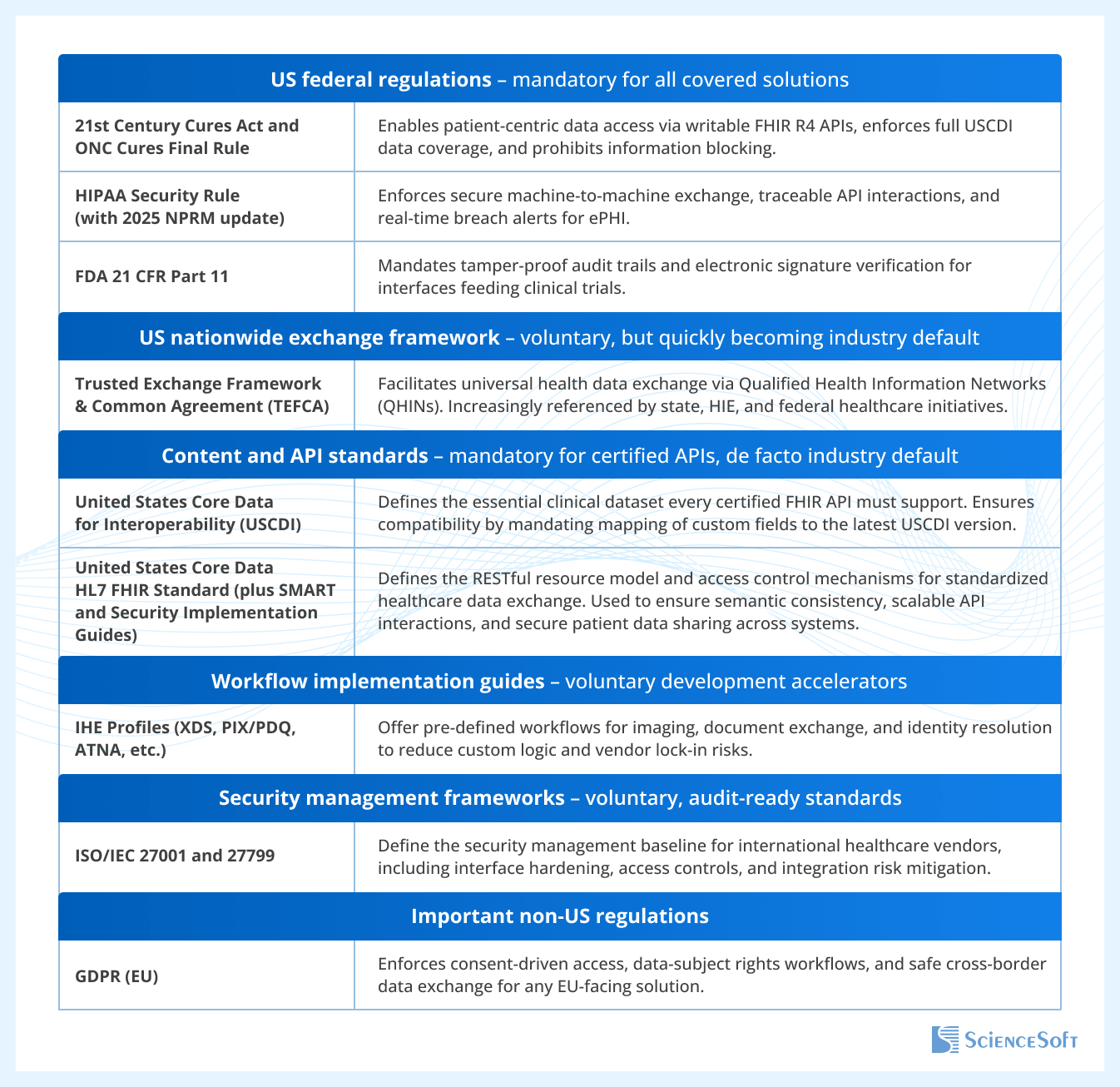
Regulatory foundations of our interoperability practices
These are the key frameworks that shape our integration approach, which ensures compliance, audit readiness, and vendor neutrality across all care settings.